
https://youtu.be/1hhr9jHFvz0?si=va2LB7MLb0UsuY1b
✯ Certified Ethical Hacker V11✯ CEH v11

How do you become an ethical hacker in 2022 before we get into the specifics of how to become an ethical hacker .
Let's define what ethical hacking is .
Ethical hacking is the use of computer and network security skills to help organizations detect vulnerabilities in their devices , networks and systems that could lead to security breaches .
Why is ethical hacking necessary ?
The United Nations reported that cyber crime skyrocketed by 600% due to the COVID-19 pandemic and cyber attacks on critical infrastructure were rated the top fifth risk in the World Economic Forum's 2020 global risks report .
Nearly every industry has had to embrace innovative solutions to cope with the threats associated with emerging technologies .
This is where ethical hackers come in .
Ethical hacking is used to counter attacks by malicious hackers by anticipating the methods that Attackers would use to break into a system .
Ethical hackers identify potential vulnerabilities so that organizations can rectify them before damage is incurred from actual cyber attacks .
Ec Council's certified Ethical hacker ce H is a certification program that equips it professionals and cybersecurity enthusiasts with the knowledge and skills .
They need to pursue a career in ethical hacking .
The CE H prepares learners for a wide range of career choices within the cybersecurity industry that offer competitive pay and rewarding recognition , cybersecurity analyst , systems engineer , network engineer , red team lead it manager and more .
The CE HV 11 covers basic to advanced hacking concepts including a deep dive into the five phases of hacking reconnaissance .
In this initial phase .
The hacker gathers as much information about the target as possible before launching the attack .
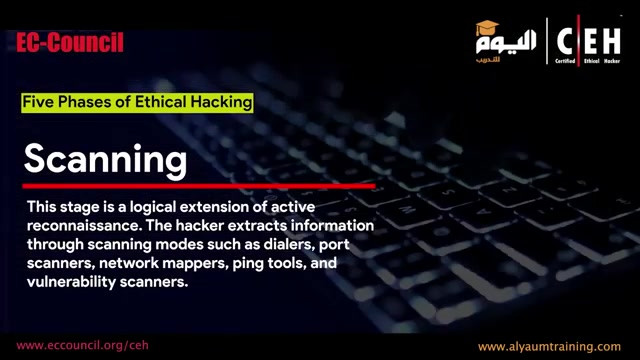
Scanning .
This stage is a logical extension of active reconnaissance .
The hacker extracts information through scanning modes such as dialers , port scanners , network mappers , ping tools and vulnerability scanners , gaining access .
In this phase .
The actual hacking takes place .
Hackers use the vulnerabilities identified in the reconnaissance and scanning stages to access the target system and network as well as associated operating systems and applications , maintaining access .
In this stage , the hacker attempts to retain their system ownership , clearing tracks .
This final phase refers to the actions that a hacker carries out to hide their hacking activity with over 20 modules and hands on interactive labs .
You'll get to build a robust foundation in cybersecurity that encompasses both theoretical and practical knowledge .


Take the first step toward becoming an ethical hacker with EC Council today , develop the skills you need to become a successful ethical hacker and build the ultimate career in cybersecurity with the CE H
Are you looking for a way to reach a wider audience and get more views on your videos?
Our innovative video to text transcribing service can help you do just that.
We provide accurate transcriptions of your videos along with visual content that will help you attract new viewers and keep them engaged. Plus, our data analytics and ad campaign tools can help you monetize your content and maximize your revenue.
Let's partner up and take your video content to the next level!
Contact us today to learn more.